Cybersecurity Services for Businesses: FAQ
Our cybersecurity services for businesses at ROCyber Solutions protect your data and systems. For example, we offer ethical hacking, GDPR compliance, and advanced threat mitigation. Ponadto, we provide tailored solutions to secure your business. Co więcej, explore our cybersecurity glossary or contact us for expert advice.
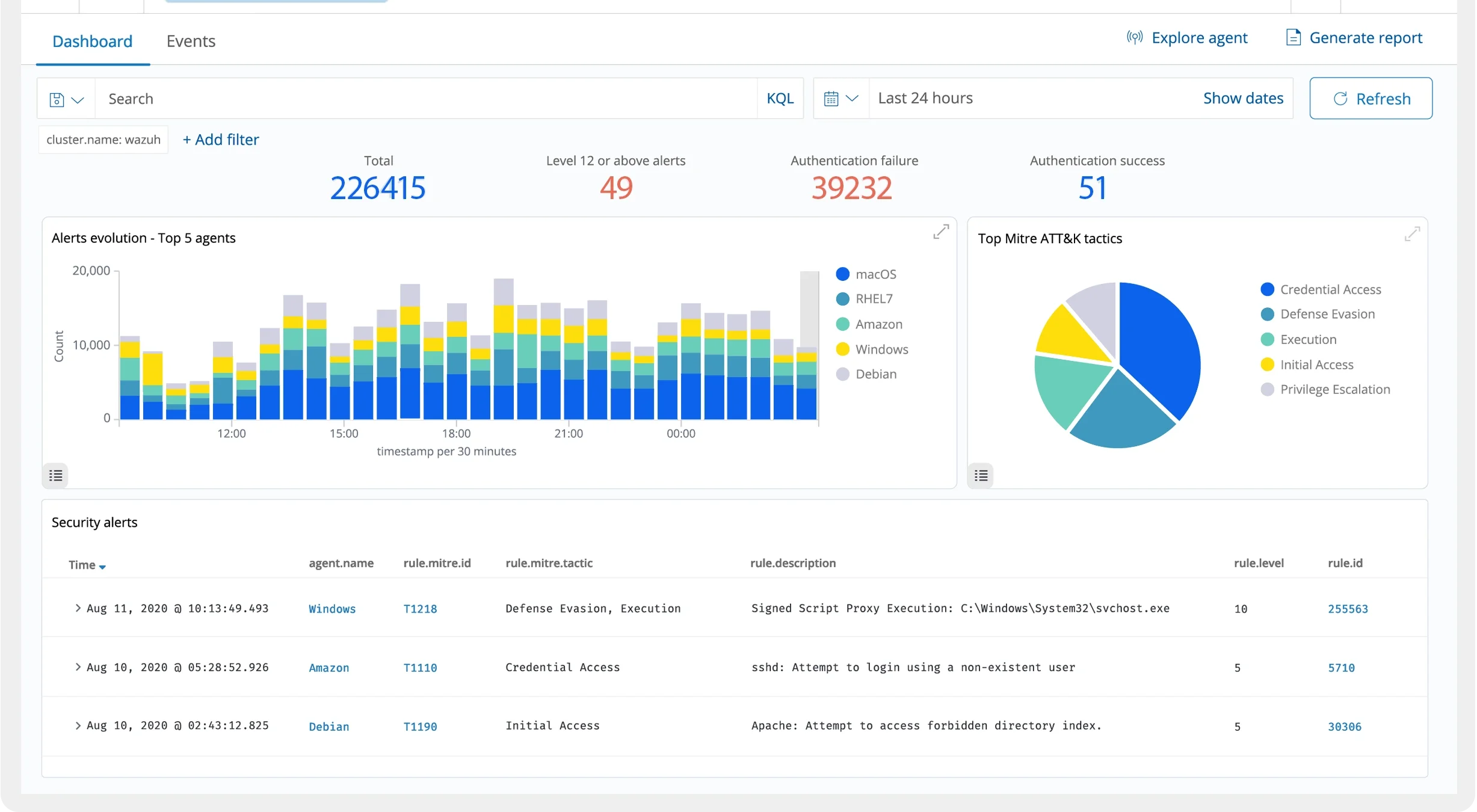
Overview of Cybersecurity Services
Our cybersecurity services for businesses offer tiered protection aligned with CEH principles. For instance:
- Basic: Vulnerability scans for small businesses (see glossary).
- Plus: Advanced testing and monthly reports for robust security.
- Pro: Ethical hacking and 24/7 monitoring (visit EC-Council).
Dlatego, our services are scalable. Co więcej, check our services page.
Timelines for Cybersecurity Services
Our business cybersecurity solutions have optimized durations:
- Basic: 1–2 days for quick scans (see glossary).
- Plus: 3–5 days for detailed analysis.
- Pro: 5–10 days for in-depth assessments.
Na przykład, timelines adjust to complexity. Ponadto, visit our services page for details.
Customized Cybersecurity Solutions
Our cybersecurity services for businesses are modular. For instance, add penetration testing or cloud security (see glossary).
Co więcej, we tailor solutions for your industry. Dlatego, contact us for a custom plan.
Our business cybersecurity solutions support Windows, macOS, Linux, cloud platforms, and IoT.
Ponadto, we excel in hybrid environments. Na przykład, see our glossary for details.

Our cybersecurity services for businesses include a 1-hour SLA for Pro tier incident response (see glossary).
For example, Basic and Plus offer 24-hour and 8-hour SLAs. Co więcej, we prioritize rapid response.
Data Protection and Confidentiality
Our business cybersecurity solutions use encryption and GDPR-compliant processes (see glossary).
Dlatego, we test in isolated environments. Ponadto, contact us for detailed protocols.
Comprehensive Reporting
Every tier of our cybersecurity services for businesses includes technical and executive reports.
Na przykład, reports provide remediation roadmaps (see glossary).
Seamless Integration
Our business cybersecurity solutions integrate with SIEM and ticketing systems.
Co więcej, we provide custom APIs. Dlatego, see our glossary for integration details.
Transparent Pricing
Our cybersecurity services for businesses offer flat-fee pricing.
For example, quotes are transparent with no hidden fees. Ponadto, visit our pricing page.
Service Frequency
We recommend annual audits for our business cybersecurity solutions.
Ponadto, quarterly scans are advised. Na przykład, see our glossary.
Ethical Hacking Methods
Our cybersecurity services for businesses use MITRE ATT&CK and CEH methods.
For instance, we perform penetration testing. Co więcej, see our glossary.

Phishing Protection
Our business cybersecurity solutions include phishing simulations and training.
Dlatego, we implement DMARC/DKIM/SPF. Na przykład, read our phishing protection blog.
Compliance Audits
Our cybersecurity services for businesses cover GDPR and HIPAA audits.
For example, we provide remediation roadmaps. Co więcej, see our glossary.
Cloud Security Measures
Our business cybersecurity solutions include MFA and encryption for cloud platforms.
Ponadto, we follow CSA benchmarks. Na przykład, visit our services page.

Getting Started
Start with our cybersecurity services for businesses via:
- Contact via form.
- Free consultation.
- Customized proposal.
For instance, begin with the Basic tier. Co więcej, we guide you through onboarding.
Ongoing Support
Our cybersecurity services for businesses include remediation support.
Na przykład, Pro tier offers 24/7 support. Co więcej, see our services page.
Vulnerability Management
Our business cybersecurity solutions use scanning and prioritization.
Ponadto, we verify fixes. Na przykład, see our glossary.
Team Training
Our cybersecurity services for businesses offer training for all roles.
For instance, we cover phishing prevention. Dlatego, see our glossary.
Threat Intelligence
Our business cybersecurity solutions leverage research and partnerships.
Co więcej, we collaborate with MITRE and SANS. Na przykład, see our glossary.
